- A TechNote on Information Security
- Dirk Racey, Private Security Investigator/Observer
A recent Boston Globe article recounted the exploits of one HD Moore, chief security officer at Rapid7, a Boston firm that fixes security flaws within IT infrastructures. (Other companies in this game are McAfee's NitroSecurity and IBM's Q1 Labs.)
Moore exploited the H.323 videoconferencing protocol to secretly tour conference rooms in law offices, venture-capital firms, oil refineries, pharmaceutical companies, hospitals and courtrooms. The latest systems from Cisco/Tandberg, Sony, LifeSize/Logitech, Polycom, Codian and others - even with encryption - were no match. And the systems Moore entered would have offered little sign of his presence, except for a tiny console light or camera movement.
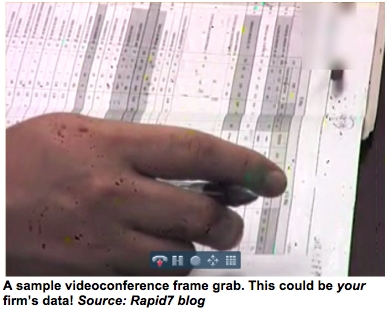 Thus, Moore warns, real cyber spies could easily gain eyeballs on your firm's sensitive information in the following ways:
Thus, Moore warns, real cyber spies could easily gain eyeballs on your firm's sensitive information in the following ways:- Zooming into areas outside conferencing rooms.
- Reading passwords from sticky notes more than 20 feet away.
- Listening to distant conversations.
- Reading email on laptop screens.
- Watching keyboards to capture passwords.
A Simple Hack
Moore used Rapid7's well-known Metasploit penetration-testing program to scan the Web for conferencing systems that:
- Sat on the Internet side of firewalls (or had been deployed in firms without firewalls).
- Automatically answered incoming IP calls.
In under two hours, after scanning 3% of the Internet, the program found 5,000 targets out of 250,000 H.323 systems examined. Moore checked a few, and crashed into an attorney-inmate confab, a medical operating room and a venture-capital meeting with financials projected on-screen.
Worse, once he cracked one system, he often could jump from its address books into business partners' conferencing rooms - even those "protected" behind security barriers. In this way, he could have invaded a highly secure Goldman Sachs boardroom, which was listed in an outside law firm's video address book.
Fend Off Coming Attacks
Moore has sounded a critical alarm. But his firm has also blogged about how the hack was done. So the race is now on to lock down your systems, pronto. Here's how:
- Assume that your videoconferencing systems have shipped in an unsecure state with auto-answer enabled. Disable it.
- If you haven't already, change systems' factory-default admin IDs and passwords.
- Move systems behind firewalls. And work with their manufacturers to add "gatekeeper" systems outside the firewalls to screen incoming calls.
- Have suppliers help you tighten their products' security and make your security auditors test it.
- Make sure systems' Web interfaces can't initiate outbound calls to outside parties.
- Require passwords of all conference participants.
- When practical, lock camera controls during and between meetings.
- During conferences, ensure that cameras can't see information on flip pads, whiteboards and computer screens that you aren't using.
- Between conferences, turn systems off (or turn mikes off and cover camera lenses).
- At all times, keep conference room doors closed.
- Before scrapping or selling conferencing equipment, thoroughly wipe its data (including address books).
Similarly, when we do start bringing smart fridges and other appliances into our homes and offices, we can also protect them (and our PCs) by changing the factory-default IDs and passwords in our own Internet routers. Many people don't, and hackers know those codes!
NOTE: For security reasons, I don't give out my email address. However, if you would like to send email to my trusted alter-ego, Dave Powell, he will deliver the messages to me in a plain brown envelope.










HD Moore's videoconferencing system pentest findings are certainly interesting, but they underscore a far more pervasive flaw in the way many people think about new networked devices - especially "smart" devices.
These are not isolated turnkey appliances that can be turned on in with little to no risk exposure. They're networked computers. Computers with access to sensitive information (here audio/video feeds, elsewhere confidential data or simply springboard access to back-end systems). As such, they need to be secured like other networked computers - assessed, hardened, firewalled, access-controlled, monitored for unauthorized use...
I think we're going to see more and more of this - for example, here's a story about a BestBuy store that recently had its SmartTVs hacked: http://bit.ly/xOiCer
From consumers to enterprise IT and employees, everyone needs to realize that networked devices shouldn't be put into place without applying at least a few basic security best practices. Skipping that step and hoping that hackers won't notice is just begging for trouble.
Lisa, yes, that's the very point. Too often, such appliances are thought to be outside of IT's purview. But the devices must be "brought in from the cold." This includes any of the new crop of smart TVs that also may be installed in public areas and conference rooms. Both the videoconferencing systems and TVs - and yes, even smart refrigerators - will merit IT's very close attention! Thanks for the great add, Lisa!