- A TechNote on Information Security
- Dirk Racey, Private Security Investigator/Observer
Last summer, I spent some quality time rebuilding my PC, all because my cat, Chomps, began sneezing. Nothing serious as it turned out, but it sent me running to a favorite pet-health site. And when the site opened in Firefox, a convincing window popped on-screen (see photo). A virus scanner I'd never heard of ("Antimalware Doctor") claimed that my machine was infected with more than a dozen threats. And to clear them, I could click the Remove Threats button.
Yeah, right. I already use two malware scanners: the full subscription version of Symantec/Norton plus the also highly rated (and free) Malwarebytes. They're great at repelling intrusion attempts and viruses in real time, but neither of them had raised a peep over the viruses that Antimalware Doctor was screaming about. So my Racey Radar leaped to Red Alert.
I Googled "Antimalware Doctor" and found that when its window appeared, my computer was already infected by a clever and dangerous "social-engineering attack" - one that waits for its victims to behave like normal human beings. This makes it hard to avoid, even if you're as compulsively suspicious as I am.
Antimalware Doctor had simply waited for me to launch a formerly trusted Web site that it had infected since my last visit. And when I did, I basically opened my computer's back door and said, "Come on in boys!"
Be On the Lookout
Infected Web sites are only one way you can be tricked into compromising your security by just being human. In fact, so many social-engineering tricks exist that your best weapon is probably hyper paranoia. In other words:
Nobody's Safe
Social-engineering attacks capitalize on the things we do every day: viewing Web pages, clicking HTML links, using window controls. But Web browsers and malware scanners are getting better at stopping these attacks. As a security sleuth, I do a ton of research. And at least twice a week, Norton/Symantec, Malwarebytes or Firefox alerts me to a link or Web site that's been reported as malicious. A year ago, they didn't do this. So kudos to them.
But social-engineering attacks are still almost unavoidable. That's another reason to use malware scanners and to keep them updated. My two scanners didn't detect Antimalware Doctor when it hit, but they did help me remove infected files afterward and have repelled several attacks since. Keep your browsers updated too. They could block the next infected site that you try to visit.
Next time, we'll explore another huge social-engineering attack tool: your email Inbox. So I'll see you then, right here under my usual dimly lit streetlamp...
Yeah, right. I already use two malware scanners: the full subscription version of Symantec/Norton plus the also highly rated (and free) Malwarebytes. They're great at repelling intrusion attempts and viruses in real time, but neither of them had raised a peep over the viruses that Antimalware Doctor was screaming about. So my Racey Radar leaped to Red Alert.
I Googled "Antimalware Doctor" and found that when its window appeared, my computer was already infected by a clever and dangerous "social-engineering attack" - one that waits for its victims to behave like normal human beings. This makes it hard to avoid, even if you're as compulsively suspicious as I am.
Antimalware Doctor had simply waited for me to launch a formerly trusted Web site that it had infected since my last visit. And when I did, I basically opened my computer's back door and said, "Come on in boys!"
Be On the Lookout
Infected Web sites are only one way you can be tricked into compromising your security by just being human. In fact, so many social-engineering tricks exist that your best weapon is probably hyper paranoia. In other words:
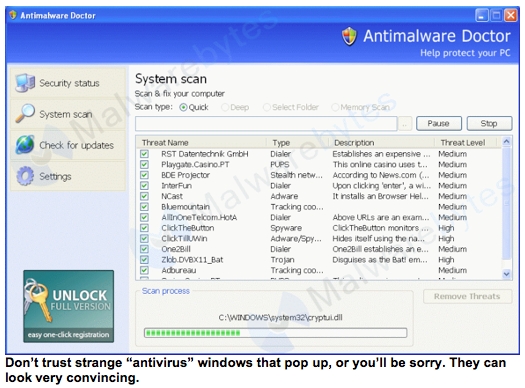 Don't fall for unfamiliar software posing as something trustworthy. The name "Antimalware Doctor," its claim to be a virus scanner and the "scanning" window that it displayed were clever ways to gain unsuspecting victims' trust and alarm them into clicking Remove Threats. As it turned out, if I had clicked anywhere in the Antimalware Doctor window (even on the red "X" to close it), more malware might have streamed into my PC, including keystroke-capture programs to report my account numbers, user IDs and passwords.
Don't fall for unfamiliar software posing as something trustworthy. The name "Antimalware Doctor," its claim to be a virus scanner and the "scanning" window that it displayed were clever ways to gain unsuspecting victims' trust and alarm them into clicking Remove Threats. As it turned out, if I had clicked anywhere in the Antimalware Doctor window (even on the red "X" to close it), more malware might have streamed into my PC, including keystroke-capture programs to report my account numbers, user IDs and passwords. - If any odd window appears on-screen, don't click anywhere in it. Don't even try to close it. Just reboot. You may lose work, but if you frequently save whatever you're doing, you won't lose much.
- Pay attention to search results. If your browser displays a different-looking or poorly formatted results page, don't click any of its links, buttons or controls. Reboot. You may have pulled in a "redirect" virus that intercepts Web searches and redirects you to its own fake results. (Apple computers aren't immune to this, either.) If you click anywhere in these redirect pages, more malware might flood in.
- Whether requests come through email, telephone, instant message, Twitter, Facebook or your front door, don't give personal information to people you didn't contact first on your own. Also suspect people claiming to represent organizations you have contacted or might normally trust. A ring of local con artists phoned my town's residents for donations to the "Police Beneficent Retirement Fund." A nice con: Who wants to hang up on the cops? But I did, and kept my bank accounts. Others didn't, and lost theirs. So make "Just say nothing" part of your personal and corporate infosecurity mantra.
- Be leery of "friending" strangers on social-networking sites or clicking links in social-network pages. Links are easily spoofed and can lead to trouble.
Nobody's Safe
Social-engineering attacks capitalize on the things we do every day: viewing Web pages, clicking HTML links, using window controls. But Web browsers and malware scanners are getting better at stopping these attacks. As a security sleuth, I do a ton of research. And at least twice a week, Norton/Symantec, Malwarebytes or Firefox alerts me to a link or Web site that's been reported as malicious. A year ago, they didn't do this. So kudos to them.
But social-engineering attacks are still almost unavoidable. That's another reason to use malware scanners and to keep them updated. My two scanners didn't detect Antimalware Doctor when it hit, but they did help me remove infected files afterward and have repelled several attacks since. Keep your browsers updated too. They could block the next infected site that you try to visit.
Next time, we'll explore another huge social-engineering attack tool: your email Inbox. So I'll see you then, right here under my usual dimly lit streetlamp...