- A TechNote on Wireless and Mobility
- Joanie M. Wexler
- Technology Analyst/Editor
Two industry trends might be magnifying a known Wi-Fi risk associated with Microsoft's widely used MS-CHAPv2 authentication protocol. The culprits are the bring-your-own-device (BYOD) and the cloud computing phenomena.
BYOD, of course, involves employees bringing personal mobile devices to work and using them to connect to corporate resources. Because employees own the devices, they might unwittingly use default settings that sidestep important security capabilities if corporate IT hasn't taken steps to enforce safe behavior.
RADIUS Validity Check
One example in the news has been the necessity to check the validity of the Wi-Fi RADIUS authentication server to which mobile devices connect. In a Wi-Fi environment protected by standard WPA2-Enterprise mechanisms, RADIUS servers can run in the corporate data center, in wireless LAN (WLAN) controllers or directly in Wi-Fi access point (APs).
Verifying the authenticity of the RADIUS server helps prevent devices from attaching to a faux access point (AP) run by a hacker. That AP basically impersonates a legitimate AP by broadcasting a service set identifier (SSID), or network name, that's listed as OK to connect to in the client device's wireless profile. The phony AP is sometimes called an "evil twin" or a "honeypot."
"The whole honeypot attack is easier to do in a BYOD setting," says Jon Green, director of government solutions for Wi-Fi company Aruba Networks. In a top-down managed environment, "all trust relationships, RADIUS servers and certificates are preconfigured to avoid honeypots. In the case of BYOD, the user will get a warning [that a server can't be verified], but end users might not heed that warning."
Evil Twin Plus CloudCracker Heightens Vulnerability
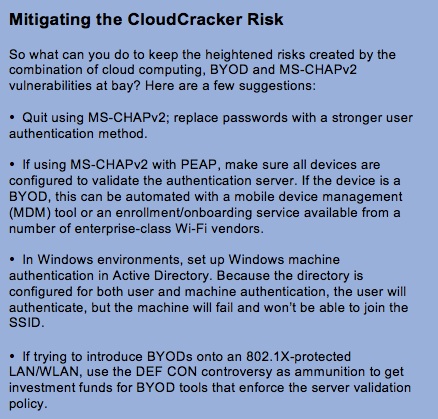 Meanwhile, the power of cloud computing enables hackers to run massive parallel computing attacks at pay-by-the-drink prices. Consider, for example, CloudCracker, an online password cracking service unveiled at the DEF CON hacker convention in July. Combine an evil twin connection with this very fast password-cracking capability, and you have the controversy that has had tempers flaring since the event took place.
Meanwhile, the power of cloud computing enables hackers to run massive parallel computing attacks at pay-by-the-drink prices. Consider, for example, CloudCracker, an online password cracking service unveiled at the DEF CON hacker convention in July. Combine an evil twin connection with this very fast password-cracking capability, and you have the controversy that has had tempers flaring since the event took place.At the convention, a long-known vulnerability in Microsoft's MS-CHAPv2 authentication mechanism was purported to pose greater risk in a BYOD/cloud computing environment. The inherent vulnerability is that, when connecting to any WLAN protected by WPA2-Enterprise, MS-CHAPv2 must be configured with the "validate server certificate" setting turned on, or it can fall prey to an evil twin connection. Ensuring that this setting is enabled is simply harder to control when the enterprise doesn't own the device.
Once the user device is attached to the evil twin, a hacker can pose as a RADIUS authentication server, intercept the user's MS-CHAPv2 exchange using a tool such as FreeRADIUS-WPE, then parse it using ChapCrack, a new tool released at DEF CON. ChapCrack returns a token containing the MS-CHAPv2 username/password hash. The hacker sends the token to the new CloudCracker service, where reportedly it can be decrypted in less than a day.
In other words, because of cloud computing's massive and more affordable compute power, it's possible to unmask user credentials and possibly gain back-door access to the corporate network more quickly than in pre-cloud days.
"It simply makes the risk of MSCHAPv2 [when not configured to authenticate the RADIUS server] riskier," says Lisa Phifer, president of Core Competence, a consultancy specializing in network and security technologies.
What's What in this Equation?
MSCHAPv2 is used both in wired virtual private networks (VPNs) and in RADIUS servers in a WPA2-Enterprise setup. WPA2-Enterprise is based on 802.1X, which specifies an authentication framework that devices connecting to wired and wireless LANs should use. But it doesn't dictate specifically which authentication protocols to use.
There are many authentication protocols for supporting a variety of user authentication methods, such as passwords, tokens, subscriber identity module (SIM) cards and certificates. However, MS-CHAPv2 is commonly used in enterprise WLANs to authenticate users with usernames and passwords. It is usually carried by the Protected Extensible Authentication Protocol (PEAP), encapsulated inside a Transport Layer Security (TLS) tunnel so that authentication messaging and credentials can't be plucked directly out of the air. In the reverse direction, Wi-Fi client failure to validate the server's certificate leaves the user vulnerable to the evil twin vulnerability, a risk now made greater by CloudCracker.
Still, because of the tunnel, many experts contend that CloudCracker has little, if any, impact on Wi-Fi security overall.
Wireless evangelist Andrew vonNagy, a senior Wi-Fi architect at Wi-Fi company Aerohive Networks, for example, wrote in a recent blog: "In a properly implemented wireless network, this MS-CHAPv2 exploit is a non-issue."
Role of Certificate Authority
When a client is configured to use PEAP-MS-CHAPv2, the client uses a secure TLS tunnel with the RADIUS server over which the user authentication happens. To ensure that the client is communicating with the genuine RADIUS server, the "validate server certificate" capability - when enabled - checks the certificate presented by the server.
The RADIUS server's certificate can be issued by a public certificate authority (CA) already trusted by every client operating system or a private CA, which requires the CA's certificate to be installed on clients. For enterprises running their own CAs, having to put certificates on every device can be a deterrent. By not enabling server certificate validation, "the result is a security hole that hackers could exploit," says Tajinder Maan, director of marketing for enterprise networking and communications at Wi-Fi company Motorola Solutions.
"Most enterprise intranet applications use a single sign-on, so the hacker could, with the username and password, gain access to intranet resources amounting to breach of confidential corporate data," Maan warns.
Motorola launched a self-service Wi-Fi enrollment system at the DEF CON conference for BYOD that pushes certificates down to client devices. Aruba and other Wi-Fi companies have similar so-called "onboarding" systems that detect when a valid user is using an unknown device and send the user to a captive portal where their devices are outfitted with the proper settings.