- A TechNote on Wireless and Mobility
- Lisa Phifer, President
- Core Competence, Inc.
Researcher Stefan Viehböck's holiday gift to the world was a personal information number (PIN) guessing attack against Wi-Fi Protected Setup (WPS). WPS is a fuss-free configuration option supported by many residential Wi-Fi routers. Reported to the U.S. Computer Emergency Readiness Team (US-CERT) in late December, this brute-force PIN crack has since been demonstrated by hundreds of volunteers running proof-of-concept attack tools.
But look-alike acronyms and diverse implementations have created confusion about real-world impact. How can you tell if this attack impacts you?
WPS, WPA, WP-Whatever
Start with what WPS is - and isn't. The "S" in "WPS" refers to "setup." Specifically, WPS is a Wi-Fi Alliance innovation, created to encourage secure wireless connections by auto-configuring Wi-Fi Protected Access (WPA/WPA2)- Personal pre-shared keys (PSKs).
Before WPS, network owners had to configure routers with long, complex WPA2-Personal passphrases (from which PSKs are derived). End users then painstakingly re-typed those same passphrases into Wi-Fi laptops, smartphones, Tivos, Wiis, etc. Mistakes proved frustratingly common, especially on consumer electronic devices without keyboards.
To greatly simplify setup, WPS auto-configures PSKs by conducting an over-the-air exchange between router and client. Depending on router make/model, setup might require typing a four-digit PIN into a client, pushing a button on the router, or holding a client up to a router that supports near-field communications (NFC). Viehböck analyzed this supposedly secure WPS exchange and found vulnerabilities that facilitate WPS PIN cracking.
However, Viehböck's attack does NOT crack WPA/WPA2 (a.k.a. 802.11i), the standards actually used to secure wireless network traffic. This means that businesses using only WPA2-Enterprise (802.1X) needn't be concerned about WPS attacks. Neither should organizations using WPA2-Personal on enterprise-grade Wi-Fi access points that don't implement WPS.
PIN-pointing the Problem
On the other hand, SMB and residential wireless router owners who use WPA2-Personal to secure their networks should be concerned and perhaps take action.
The brute-force attack reported by Viehböck reduces the number of PINs that a would-be intruder must try before correctly guessing a WPS-enabled router's PIN. For some routers, worst-case time-to-crack is roughly four hours. For other routers, cracking could take up to 90 days - or even forever. Having cracked a router's WPS PIN, the intruder can freely connect any new client, gaining access to other connected systems and uplinked networks just like legitimate clients.
Why the range in attack duration? A brute-force attack works by repeatedly trying all possible combinations until the right PIN is guessed. Some routers ignore WPS failures, letting an attacker keep on plugging without delay. Other routers respond to repeated failures with some sort of "lockdown" period during which WPS attempts are ignored. Maximum time-to-crack depends on how many failures are permitted, how long the lockdown lasts and whether manual action is required to re-enable WPS. Furthermore, some routers engage in WPS for only a few minutes after the owner explicitly enables this auto-configure option.
Protect Yourself
Unfortunately, the affected Wi-Fi routers are relatively easy to attack; proof-of-concept tools are already freely available. Furthermore, initial (not necessarily representative) surveys indicate that about one-quarter of all Wi-Fi routers now using WPA/WPA2-Personal could be vulnerable. For those unlucky enough to be vulnerable, quick action is warranted. Fortunately, the remedy might be easy.
Anyone using a residential or SMB Wi-Fi router with WPA/WPA2-Personal should start by determining whether the router's make/model even supports WPS. A list of Wi-Fi-certified WPS-capable products can be found at www.wi-fi.org. Those with non-Wi-Fi certified products should browse product configuration guides or screens, looking for a function that sounds like WPS but might be called something else.
Those using routers that support WPS should dig further to determine actual risk exposure and ways to reduce or eliminate it. A community-sourced list of volunteer-tested routers (by make, model and firmware version) has been shared here at Google Docs. In particular, note the "WPS can be disabled" column, which describes whether, and sometimes how, to turn WPS off in each tested router.
Further information about this attack, affected products and recommended workarounds has been published by the US-CERT here. Ultimately, vendors selling especially vulnerable WPS-capable products might release updated firmware to add lockdown mechanisms or take other steps to deter this attack. In the meantime, turn WPS off wherever possible, or enable WPS only when actively attempting to auto-configure a new client.
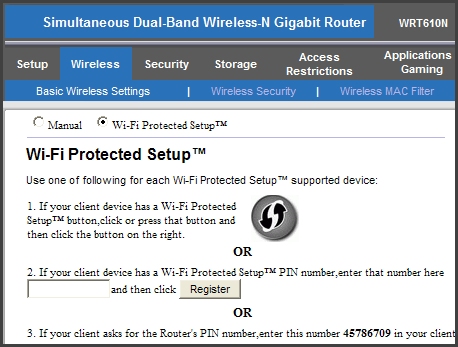 Shown are WPS options in a common residential Wi-Fi router. Remedies to deter attack vary by product; here, just choose "Manual" in lieu of PIN or push-button auto-configuration.
Shown are WPS options in a common residential Wi-Fi router. Remedies to deter attack vary by product; here, just choose "Manual" in lieu of PIN or push-button auto-configuration.
But look-alike acronyms and diverse implementations have created confusion about real-world impact. How can you tell if this attack impacts you?
WPS, WPA, WP-Whatever
Start with what WPS is - and isn't. The "S" in "WPS" refers to "setup." Specifically, WPS is a Wi-Fi Alliance innovation, created to encourage secure wireless connections by auto-configuring Wi-Fi Protected Access (WPA/WPA2)- Personal pre-shared keys (PSKs).
Before WPS, network owners had to configure routers with long, complex WPA2-Personal passphrases (from which PSKs are derived). End users then painstakingly re-typed those same passphrases into Wi-Fi laptops, smartphones, Tivos, Wiis, etc. Mistakes proved frustratingly common, especially on consumer electronic devices without keyboards.
To greatly simplify setup, WPS auto-configures PSKs by conducting an over-the-air exchange between router and client. Depending on router make/model, setup might require typing a four-digit PIN into a client, pushing a button on the router, or holding a client up to a router that supports near-field communications (NFC). Viehböck analyzed this supposedly secure WPS exchange and found vulnerabilities that facilitate WPS PIN cracking.
However, Viehböck's attack does NOT crack WPA/WPA2 (a.k.a. 802.11i), the standards actually used to secure wireless network traffic. This means that businesses using only WPA2-Enterprise (802.1X) needn't be concerned about WPS attacks. Neither should organizations using WPA2-Personal on enterprise-grade Wi-Fi access points that don't implement WPS.
PIN-pointing the Problem
On the other hand, SMB and residential wireless router owners who use WPA2-Personal to secure their networks should be concerned and perhaps take action.
The brute-force attack reported by Viehböck reduces the number of PINs that a would-be intruder must try before correctly guessing a WPS-enabled router's PIN. For some routers, worst-case time-to-crack is roughly four hours. For other routers, cracking could take up to 90 days - or even forever. Having cracked a router's WPS PIN, the intruder can freely connect any new client, gaining access to other connected systems and uplinked networks just like legitimate clients.
Why the range in attack duration? A brute-force attack works by repeatedly trying all possible combinations until the right PIN is guessed. Some routers ignore WPS failures, letting an attacker keep on plugging without delay. Other routers respond to repeated failures with some sort of "lockdown" period during which WPS attempts are ignored. Maximum time-to-crack depends on how many failures are permitted, how long the lockdown lasts and whether manual action is required to re-enable WPS. Furthermore, some routers engage in WPS for only a few minutes after the owner explicitly enables this auto-configure option.
Protect Yourself
Unfortunately, the affected Wi-Fi routers are relatively easy to attack; proof-of-concept tools are already freely available. Furthermore, initial (not necessarily representative) surveys indicate that about one-quarter of all Wi-Fi routers now using WPA/WPA2-Personal could be vulnerable. For those unlucky enough to be vulnerable, quick action is warranted. Fortunately, the remedy might be easy.
Anyone using a residential or SMB Wi-Fi router with WPA/WPA2-Personal should start by determining whether the router's make/model even supports WPS. A list of Wi-Fi-certified WPS-capable products can be found at www.wi-fi.org. Those with non-Wi-Fi certified products should browse product configuration guides or screens, looking for a function that sounds like WPS but might be called something else.
Those using routers that support WPS should dig further to determine actual risk exposure and ways to reduce or eliminate it. A community-sourced list of volunteer-tested routers (by make, model and firmware version) has been shared here at Google Docs. In particular, note the "WPS can be disabled" column, which describes whether, and sometimes how, to turn WPS off in each tested router.
Further information about this attack, affected products and recommended workarounds has been published by the US-CERT here. Ultimately, vendors selling especially vulnerable WPS-capable products might release updated firmware to add lockdown mechanisms or take other steps to deter this attack. In the meantime, turn WPS off wherever possible, or enable WPS only when actively attempting to auto-configure a new client.
 Shown are WPS options in a common residential Wi-Fi router. Remedies to deter attack vary by product; here, just choose "Manual" in lieu of PIN or push-button auto-configuration.
Shown are WPS options in a common residential Wi-Fi router. Remedies to deter attack vary by product; here, just choose "Manual" in lieu of PIN or push-button auto-configuration. 












You forgot to mention the core vulnerability of the WPS pin. Namely that the 8 digit pin is divided into 3 parts. First 4 digits compose the first part, 5th to 7th digit compose the second part and the 8th digit is a checksum. Check sum is precomputed for ever possible 7 digit pin combination so cracking it is not required by reaver. Nextly when the first 4 digits are wrong the router will respond with an M5 error, if they are correct but the 3 following digits are wrong then it will respond with an M5 message and an M7 error. In essence this flaw cuts down possible pin attempts from 100,000,000 to 11,000. Assuming 4 seconds per pin attempt cracking an 8 digit pin would take up to 12.68 years, cracking whats in essence two pins 4 digits and 3 digits each at 4 seconds per attempt would only take up to 12.22 hours.
In addition some routers (such as Netgear and Linksys) do not allow you to turn off WPS. Even if you disable WPS in settings the router will still continue to accept WPS PINs and so is still vulnerable. The only hope than is that the vendor will update the firmware to fix the security hole, or you can flash the router with a firmware which does not support WPS at all -- DD-WRT for example.