- A TechNote on Information Security
- Dirk Racey, Private Security Investigator/Observer
- Today, a seven-character password containing only numbers can be cracked almost instantly.
- Add in upper- and lower-case letters, and that password can be broken in less than 10 hours.
- Mix in special characters, and the password might survive eight days.
- Then add a character, and your new eight-character password could hold out for from 10 seconds to as long as a couple centuries, depending on its content. (NIST, the National Institute of Standards and Technology, averages its survival at about 16 minutes.)
These stats apply to hackers' simplest brute-force methods, which test every combination of characters until they hit a password that works. But today's Hackerverse mob has even faster, more persuasive tricks and tools to make passwords spill their guts, including:
- Automated lists of commonly used (dumb) passwords, like password, 123456, abc123, querty, monkey, iloveyou, trustno1, master, admin, mustang and adminpassword.
- "Dictionary Guesser" programs that throw ordinary words (like football) at login screens in their native languages.
- "Hybrid Guessers" that append strings like abc, 123, 01 and 02 to dictionary words.
- Mass theft (and sometimes public release) of tens of millions of active passwords. We've seen it happen recently with Zappos, Sony, Yahoo, Gmail, Hotmail, AOL, LinkedIn, eHarmony and others.
- Throwing hacked or stolen passwords at other sites (which works because more than 60% of people unwisely use the same passwords on multiple sites).
- Networked turbocharged hardware that collaborates to accelerate all of the above.
With these in the game, a nine-character password that at one time might have taken brute-force tools thousands of years to crack could now fall in minutes or hours. So how secure are the five- to eight-character alphanumeric passwords that 70% of us still use?
Strength Necessary, But Not Sufficient
Yes, passwords are dead (or at least dying) simply because they are ASCII strings. And regardless of their strength, TechRepublic is calling 2012 "The Year of the Password Theft." Hackers are cracking, stealing and sharing passwords so fast, thefts this third-quarter are running 300% above 2011's numbers. Looked at another way, a recent survey of 583 U.S companies found that 90% of respondents' computers were hacked at least once during the past year. This situation will only degrade as hackers grow more creative and their tools increase in power.
So what can you do to protect your passwords and identity? Common wisdom says that passwords:
- Should be at least 10 characters long (and preferably 12 to 16).
- Should mix numbers, mixed-case letters and special characters.
- Shouldn't contain personal data like names, addresses or birthdates, or words that can cave to Dictionary Guessers.
- Shouldn't be simple variants of passwords you've used before, like mypassword01, mypassword02 and mypasssword03 (for if cyber thugs crack one version, they'll try others).
Some suggest that mnemonics may produce the strong passwords of tomorrow. For example: the phrase "Give me liberty or give me death" would become Gmlogmd. Passwords like these would be easy to remember and might even slow some of the hackers' fancier tools. But mnemonics are still ASCII strings that would fall to brute-force guessers and outright theft just as rapidly (or slowly) as other passwords of the same length and content.
So password strength is rapidly becoming a weak barrier.
Users Not Helping
Beyond such tech issues, human factors aren't helping. People still:
- Use short, weak and even well-known stupid codes like password, 123456, admin and monkey, which are easy to remember and even easier to crack.
- Use simple variants of one password, which compromises all variants if any of them is guessed or stolen. (Your access-control systems should force users to change their passwords regularly, but simple variants of previous passwords shouldn't be allowed.)
- Use the same password on multiple accounts including (dangerously) social networks. (The reported average seems to be 6.5 passwords for every 25 accounts.) This makes it much easier to steal identities and trash peoples' e-lives when a password is stolen from any one of the user's accounts.
- Share passwords with others.
- Respond to phishing emails from "trusted" organizations like Facebook, claiming that they need to click a link to reset their password. (Users should do this only through their personal account pages, not through emailed requests.)
Some of these factors, (like the first two) can be tightened with security technology. But IT managers must also address those that can't (like the last three) with published policies and procedures for all data devices used in the organization.
Yes, strong passwords remain important. But Web sites and ecommerce systems still use passwords more than any other type of access control. So people must continue to use (or start using) very strong ones.
Serious Times
All industries need to pay attention to the password problem. But the Norton Cyber Crime Index has identified four sectors that have recently experienced the most password-based identity theft: computer hardware (31.6% of ID thefts), telecommunications (22.2%), software (17.6%), and government (12.4%). IT departments in these industries (plus finance, which is always a target) should be especially concerned about how their systems assign and manage passwords.
It'll only get worse. Bill Gates may have warned us before we were ready to hear. But passwords' death knell is sounding even more strongly today. The password controls that make us feel safe now are growing more and more porous. They're becoming Trojan Horses outside (and inside) our walls. Horses of a different color. Horses of our own making.
Next month, we'll discuss some common IT procedures that may be making the situation worse, and about potentially stronger access controls that are being tested. See you then!
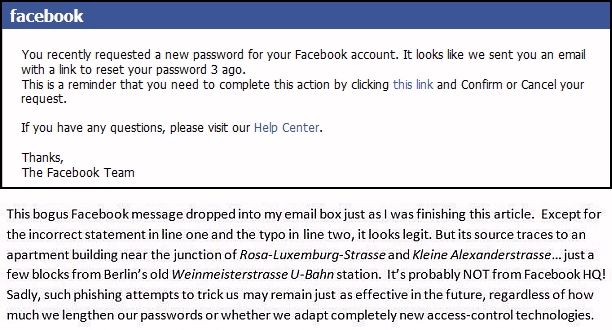













Lately, I’ve wondered whether the so-called “strong” passwords (like 71_8+#hjI*6Nb) are any more secure than “weak” ones of the same length (like adminpassword). With hackers using automated guessers like Cain and Abel, ElcomSoft, Hashcat, Hydra and John the Ripper, aren’t all passwords of the same length as statistically secure (or insecure) as each other?