- A TechNote on Information Security
- Steven Taylor, Editor-in Chief, Webtorials



For a few non-CAPTCHA methods of deterring comment spam, look here.
People do not "waste" their time doing this at all: its normally all done by software (search scrapebox or GSA search engine ranker) and the idea is that people leave a comment and the comment will contain a link to their website.
So I am very surprised at that comment in this article "At Webtorials, we find it difficult to understand why somebody would spend the energy to fill in comment forms with bogus information in the first place"
Often the username will be the keyword they are trying to rank for... its simple a way to try to improve a websites ranking.. Google see's the comment and the link to the website and it's a backlink.. Simple as that really..
Not everysite moderates comments like you do..
As an aside... I haven't had to enter a captcha to leave this comment.
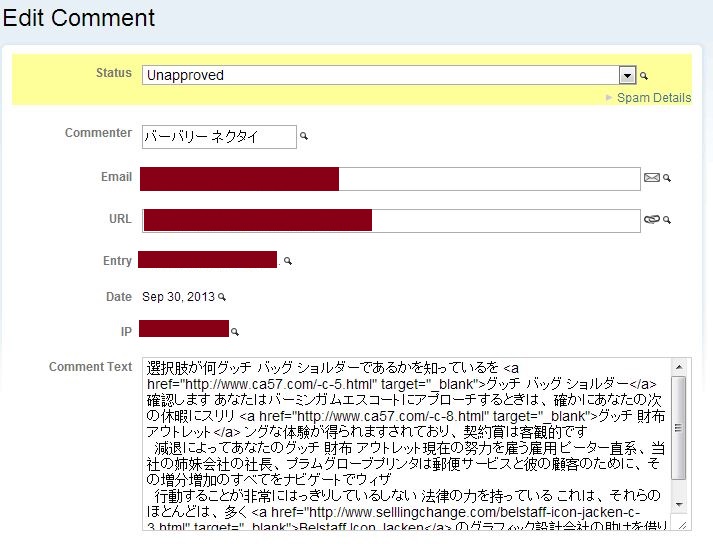
The motivation in this case appears to be advertising. Take a look at the URLs in the comment text of the post. For example, http://www(dot)ca57(dot)com/-c-8.html, is advertising women's handbags - probably counterfeit handbags.
[This is in reference to the comment "We love our information at Webtorials, but we're giving it out for free, so it's not exactly like breaking into a bank account."]
An alternative to proving that end user is human is to check and sanitize the input for comments to eliminate javascript, binary characters, etc. Essentially, consider that comments should be text only, not other stuff. This is the approach that Web Application Firewalls (WAF) take. You do have a WAF protecting your site don't you?
Indeed, SEO (Search Engine Optimization) does seem to be the primary motivation for spamming comment fields, so thanks to both Karl and David!
No, Karl, we do not have a WAF per se. There's not enough traffic. But we do have some pretty stringent restrictions set to make sure that links in comments don't get searched. However, this does seem appropriate for larger enterprises. Also, you will notice that I edited your comment to use (dot) as the separator so the URL did not get searched.
Of course, this raises the entire question of both the efficacy and the ethics of SEO as a common business practice. I had intended to mention this topic as a point-of-interest only, but I am becoming convinced that it deserves a TechNote of its own.
What if you required each person to have an account and to login to the account before being able to post a comment? Wouldn't this method work? I don't think that bots have accounts.
Requiring usernames and accounts would VERY significantly if not totally stop spammed comments. You are precisely correct.
However, over the past two years, we have made significant attempts to eliminate the need for usernames and passwords, both for accessing Webtorials and for commenting at Webtorials.
Our reasoning is twofold. First, we are trying to create an open community where people can participate easily. Requiring that users remember yet another username/password (and our having to maintain username/password files, lookups, etc.) is in contrast to our trying to promote this open community.
Second, there is a security risk the we would like to avoid. Many people use the same username and password for several or even many sites. If any one of the sites where usernames and passwords are stored are compromised, then there is a possible security breach for many sites.
For more on advanced authentication methods, we just published a Practical Methods for Improving Authentication.
I read somewhere that some organizations were using CAPTCHAs as a crowd-sourcing means of validating the machine (sic!) digitalization of historical (typed?) documents to expand the content of historical material available online. (Images typically in courier type-face, admittedly rarely used in today's CAPTCHAs). So whilst CAPTCHAs might be annoying, and ineffective as an authentication method, at least I could see that there was some benefit to them.
"Eight Alternatives to the Hated Captcha" and, for the more technically oriented, "10 Things to Check Before Using a CAPTCHA" give some inventive suggestions. I would love to hear from our readers as to how you are planning to deal with authentication alternatives.