- A TechNote on Wireless and Mobility
- Lisa Phifer, President
- Core Competence, Inc.
Nonetheless, NPD In-Stat expects hotspot use to reach 120 billion connections by 2015. One reason is that mobile operators are anxious to offload 3G/4G by collaborating with vendors to backfill hotspot gaps.
Let's take a look at two closely related programs - Wi-Fi Alliance (WFA) Passpoint and Wireless Broadband Alliance (WBA) Next-Generation Hotspot (NGH) - to learn what enterprises can expect from hotspots in 2013 and beyond.
Passpoint: Outfitting the Players
According to WFA spokesperson Kevin Robinson, "Passpoint is a Wi-Fi certification program, bringing cellular-like roaming to mobile devices that visit Wi-Fi hotspots."
Specifically, Passpoint will test Wi-Fi clients and access points that implement the Hotspot 2.0 specification. That spec melds IEEE 802.11u (an 802.11 amendment with features for improving Wi-Fi interworking with external networks) with WFA Voice-Enterprise and WPA2-Enterprise certifications to automate hotspot discovery and selection, streamline authentication, protect data and support both inter-provider roaming and on-demand access.
How will Passpoint work? Picture a dual-mode smartphone, chowing down on 3G bandwidth when entering a Wi-Fi hotspot.
- Via 802.11u protocols, the phone learns about available hotspot capabilities, including network services and inter-provider agreements. From there, it can make an automatic policy-based decision about whether or where to roam.
- To roam, the phone mutually authenticates with a selected hotspot using a Passpoint-supported 802.1X Extensible Authentication Protocol (EAP) type: SIM, AKA, TLS or TTLS. SIM and AKA reuse the phone's cellular credentials, while TLS and TTLS use certificates or passwords.
- Once authenticated, the phone and hotspot exchange keys used by WPA2-Enterprise to stop over-the-air data eavesdropping or replay.
- Inter-provider agreements play a critical role, letting hotspots interact with proxy-operated hubs and mobile operator servers to enable payment for authorized services (see WBA). Passpoint hides this from hotspot subscribers with one exception. If the phone does not already have an account, Passpoint supports on-the-spot setup.
Users can still connect manually to hotspots by typing passwords into a portal before launching a VPN client. But users that subscribe to a roaming service get to skip these tedious, error-prone steps, auto-connecting any Passpoint-certified device to any trusted hotspot outfitted with Passpoint-certified infrastructure.
According to Robinson, Hotspot 2.0 plugfests (trials to debug specs and products) are now underway. The Passpoint program will launch in mid-2012; early certified products will ship soon after. However, given the sheer number of players engaged in this symphony, don't expect Passpoint ubiquity anytime soon.
Next-Generation Hotspot: Conducting the Orchestra
In fact, one might dismiss Passpoint as overly ambitious were it not a lynchpin in the WBA's NGH program. Mobile operators are struggling to meet skyrocketing 3G demand; 4G escalates competition for inherently limited resources. An offload solution is badly needed; NGH offers that salvation.
WBA members include both fixed broadband operators and the world's top mobile operators, including AT&T, DoCoMo, Orange and T-Mobile. Combined, these players operate nearly 300,000 Wi-Fi hotspots worldwide.
"We're an operator-centric organization, focused on using Wi-Fi from a services perspective. We're driving NGH to help operators establish roaming interoperability and integrate Wi-Fi into core networks," says WBA CEO Shrikant Shenwai.
NGH builds upon past WBA programs: Wireless Roaming Intermediary eXchange, or WIX (2007) and WISPr 2.0 (2009).
"WIX created a backend specification that operators now use to enable roaming [throughout] an ecosystem. With WISPr, we learned how to use 802.11 and 802.1X," explains Shenwai. "NGH starts with Hotspot 2.0 and details how to deploy seamless roaming in an end-to-end carrier environment."
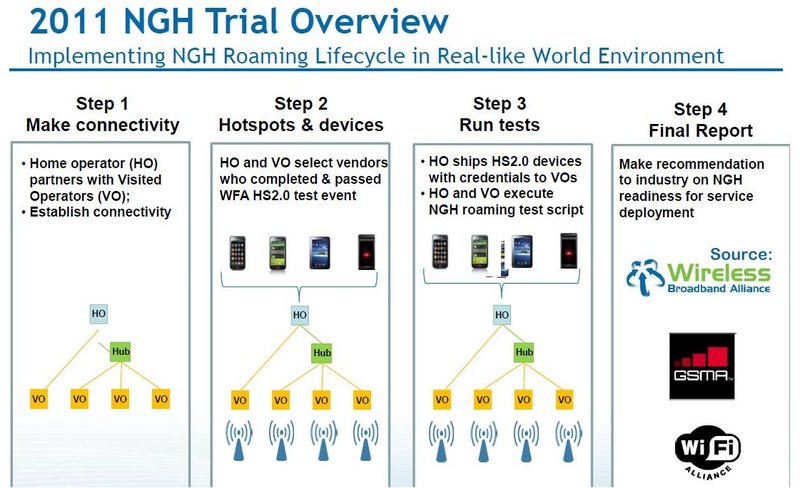
But NGH is far more than a vision for 3G/Wi-Fi roaming. According to business workgroup chair Tiago Rodrigues, the WBA has completed an NGH Operators Guide, detailing seamless authentication and 3G/4G offload best practices, with implementation and business implications. A series of real-world trials achieved their target in November 2011, and a final report is expected "within weeks."
"We conducted end-to-end tests in production environments, implemented by key industry players," said Rodrigues (see figure at bottom).
- Step 1 verified 3G roaming between visited and home network operators and via hub providers such as TNS.
- Step 2 added Wi-Fi hotspots, using devices from vendors such as Cisco and Ruckus that implemented Hotspot 2.0.
- Step 3 conducted more extensive real-world tests between providers such as Orange and SMART. The final report will document lessons learned by the 16+ operators and vendors that passed NGH tests.
While NGH is ambitious, it has been proven in trials with participants anxious to earn revenue and cut costs through Wi-Fi offload. Yes, ubiquitous roll-out will take time (think 3G). And thorny details such as roaming policy must be worked out. But enterprises should expect mobile operators to start pushing Passpoint/NGH services in 2013. Early adopters might start by enrolling international travelers most likely to reap tangible transparency and security benefits.














It seems like these smart/secure hotspot efforts eventually could be applied to deliver to enterprises what we used to call "fixed-mobile convergence" (FMC) - more accurately called "mobile-mobile convergence." For enterprises, the goal is/was to transition users from cellular to private Wi-Fi when possible for cost reasons and then back to cellular when that's all that's available. The on-premises solution to this problem didn't really take off, but if the smarts are already in the network to help carriers offload cellular traffic and keep users connected and happy (and assuming the right associations at the back end are made), it would seem that an enterprise flavor of this setup could eventually work, too.