Last month,
I suggested that password technology as we know it, is growing
increasingly obsolete and dangerous. Its effectiveness is shredding
against the Hackerverse's growing onslaught. Using longer, stronger
passwords will continue to hold cyberthugs back for a little while
longer, but even strings that should take millennia to guess are now
falling instantly to phishing attempts and bulk theft. The biggest
problem with passwords isn't that they are short and stupid (though many
are). It's simply that they are alphanumeric strings, which are growing
easier and easier to guess, steal and share.
This
is also true of the usernames/IDs that accompany most passwords! Being
alphanumeric, they too are very easy to guess, steal and share. And many
IT departments aren't helping the problem. Often what should be a
two-stage security barrier rests on passwords alone.
Dangers Not Discussed
Several
dangerous password-related practices aren't often discussed, but should
be. Fortunately, these practices can be addressed by IT systems,
programmers and webmasters.
The first is the
Web's own attempts to force users toward less secure passwords. Before I
took my business elsewhere, one of my banks didn't let me use special
characters in my password. Either their IT department or their webmaster
was actually forcing me to compromise both my account's security and
the bank's as well. If your organization slaps similar restrictions on
its internal or external users, consider stopping now.
The
second issue lies outside passwords themselves. In today's risk
environment, usernames/IDs should be as strong and difficult to guess as
the passwords that accompany them. Yes, it'd be impractical to expect
people to remember codes like:
- Username/ID: sxi87G_fhs-*b_5v
- Password: 71_8+#hjI6Nb1_hj
There
are password-management systems that could make it easier to implement
and enforce high-strength usernames and passwords throughout the
organization, without making users struggle to remember them. I will
get into detail about those programs later in this TechNote.
And a third infrequently discussed issue is that corporate access-control systems actually may be endangering
their own networks and intellectual assets because they make employees'
usernames/IDs easy for hackers to guess. To illustrate, let's say I'm a
hacker with your firm in my crosshairs. I want to steal your employees'
access codes, your corporate data and perhaps even a few personal
identities while I'm at it. And you just may have rolled out the carpet
for me. Here's what I'd do:
- I'd first look up your firm's "About Us" and "Contact Us" Web pages.
- I'd
note any employee names and email addresses that they show. (Some email
addresses will appear in plain text, while others might open in an
email system like Outlook when an individual's name is clicked.)
- If your firm is one of the many that automatically assigns employee email addresses (and even internal usernames/IDs) using consistent formats like dracey or dirk.racey,
I can now guess the email addresses and usernames/IDs of any other
employees and executives whose names I also happen to know. (And I can
find many more names... plus perhaps more internal usernames/IDs... by
trolling your corporate blogs.)
- With this data in hand, I can launch my brute-force hacking tools against your employees' login screens.
- And
while my PCs are brute-forcing their way into your employees' accounts,
the fragments of data I've already got can be leveraged into other sorts of identity theft.
This
scenario shows that if you let users create their own insecure
IDs/passwords, or your systems automatically generate internal usernames
and email addresses with predictable formats like dracey or dirk.racey@ourmail.com,
you are giving hackers and identity thieves the keys to your servers
and networks. For unlike passwords, usernames/IDs and email addresses
often appear in plain text on the Web. And if your login formats are
consistent, the Hackerverse can guess other employee IDs and email addresses from any single exemplar. In a world where even parts of names or email addresses can be leveraged to steal data and identities, such format consistency is naïve at best.
Tech to the Rescue?
Password-management
systems can help to some extent. They let users access multiple
resources using very strong (and sometimes even encrypted) codes that
need not be remembered. Such systems include:
They're
a great idea, and I'd love to let one of them corral my own nightmarish
cloud of uber-strong passwords. But I remain paranoid that some
faceless cybernut might crack my access into this gateway system and
torch my entire digital life. Yes, vendors assure us that their products
are secure. But when hackers and identity thieves steal data (including
passwords) even from tightly guarded systems in the CIA and from
security organizations like RSA and the FBI-affiliated InfraGard
(twice), one suspects that no system or product is ever completely safe.
Other
broader systems can also help, by managing passwords and enforcing
password policies and procedures. These include (among many others):
But
I fear that our future security requires that we thank usernames and
passwords for their decades of service, and move on to access controls
that depend more on human actions than on alphanumeric strings.
Coming Alternatives
The
world is already moving from alphanumeric strings toward "graphical
logins," which are usually images that users must manipulate to gain
access.
One of the first such
tools--CAPTCHAs--displayed text blocks that users had to decipher. But
while these were great in the '90s,
they can be cracked today
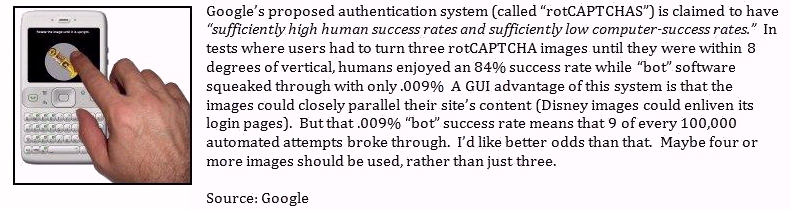
So Google (which acquired reCAPTCHA in 2009) has been testing an updated version, called
rotCAPTCHAs,
that displays randomly rotated photos of everyday objects. Users must
turn each image to within 8 degrees of vertical... a visual process that
(theoretically) is tough for hackers to code. But it's a work in
progress, as the accompanying photo/caption indicates.
The latest Android and Windows 8 devices are also trying their own new alternatives, but
McAfee recently demonstrated security issues with the Android approach. And Win-8's new "
Picture Passwords"
have also come under fire. These require users to perform predefined
taps and finger swipes on an image to gain access. So before bringing
Windows 8 devices into the enterprise, check out recent cautions in
Computerworld and
elsewhere.
Two additional things also bug me about Microsoft's Picture Passwords:
- One
must still enter a traditional password before creating a Picture
Password, but only the Picture Password seems to be needed to unlock a
device or account.
- Picture Passwords may simply be too cool for
their own good! I could see people showing off their Picture-Password
cleverness to friends, relatives or even co-workers. And such sharing
would be highly unwise.
The National
Institute of Standards and Technology is also getting into the act. They
are funding grants (of from $1.25 to $2 million per year for up to two
years) to develop and market better controls that are stronger than IDs
and passwords. It's part of their
National Strategy for Trusted Identities in Cyberspace.
This is, at least, encouraging. A promising alternative that's already
being suggested is an app that turns mobile phones into physical
authentication tokens. In its favor, this wouldn't force people to buy
new hardware...which might overcome non-commercial users' resistance to
physical tokens and biometric screens. But any such system must be able
to shut itself down fast if a phone is lost or lifted.
These
are just a few ideas for future access controls. But until any new
approach is widely adopted, we can't entirely blame hackers and identity
thieves for stealing our digital lives. We're still making it
soooooo
easy for them! Until we dramatically tighten (or change) the way we
authenticate users, alphanumeric usernames and passwords will remain
Trojan Zebras of a markedly different color... parked outside (or
inside) our digital thresholds, hiding unpleasant surprises within, and
of our own making.














What about Open Source password managers like Clipperz, KeePass, Password Gorilla, Universal Password Manager, and Yadabyte Passwords? Are they safe?