- A TechNote on Unified Communications
- Gary Audin, Delphi, Inc.
Should you be considering SIP trunking as an alternative to traditional PSTN connections such as T1 and ISDN Primary Rate Interface (PRI) services? After all, the Session Initiation Protocol (IETF RFC 3261) is widely promoted as a way for enterprises to lower costs and offer new and better services.
But before you embark on the path of SIP trunking and SIP phones, it's useful to know what SIP is and how it's used, along with some advantages and potential concerns.
What SIP Does and Doesn't Do
Although often thought to be intended specifically for use with voice-over-Internet- Protocol (VoIP) communications, SIP can also be used to establish and control video, instant messaging (IM), file transfer, games and other media sessions. It is used in computer-telephony integration (CTI) applications, connecting IP telephony systems to enterprise server applications such as IBM Sametime and Microsoft Office and Lync products. Some IP PBX vendors use SIP to communicate with VoIP gateways, others for trunking between their IP PBXs.
SIP has five main functions: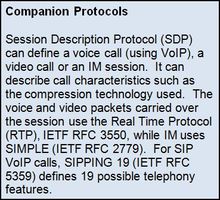
SIP does not define a phone call. Rather, a complementary protocol, the Session Description Protocol (SDP) in IETF RFC 4566, defines the many forms of multimedia to be carried over the SIP connection (see box).
Replacing the Local PSTN Connection
As an alternative to traditional PSTN connections, SIP allows the enterprise's IP PBX to communicate directly over an IP connection provided by a SIP trunking service provider, eliminating the need for a enterprise-resident gateway device. The service provider performs the VoIP-to-PSTN conversion.
Key reasons for moving to SIP trunking are lowering costs compared to T1/PRI trunks by 10% to 70%, according to some providers; the ability to offer new services such as combined Internet and voice services; and the ability to offer services in more flexible ways. The enterprise can subscribe to any number of voice connections in small increments from 2 to 700 lines per SIP trunk rather than 24 lines at a time for a T1 connection.
But SIP trunking isn't quite "plug-and-play." Especially during its first year of use, SIP can generate more trouble tickets than T1/PRI trunks because of potential SIP and codec interoperability failure and call-quality issues, which are all highly dependent on the service provider and your premises equipment. Both IP PBX and service provider interface configurations may not match.
Because of the interoperability concerns, it is critical to know whether the prospective SIP trunking provider supports the SIPconnect Technical Recommendation, a standards-based approach for IP peering between SIP-enabled IP PBXs and VoIP service provider networks.
Some vendors have developed their own proprietary SIP trunking support mechanisms that are not compatible with SIPconnect. Before connecting to a service provider, make sure that the provider supports true SIPconnect interoperability rather than a non-standard version of this trunking protocol.
What About Security?
Security is a major concern with SIP trunking. Like any other Internet connection, the SIP trunk should operate through a DMZ. Many SIP users have embraced the Session Border Controller (SBC) as better suited than typical firewalls to providing a security solution. An SBC provides:
Beware of Proprietary End Points
Traditionally IP PBX vendors have developed their own protocols for use with their own brands of IP phones; in addition, Skype and some other voice services have proprietary protocols with SIP-like functionality. As an array of third-party vendors has emerged with new IP phones, most IP PBX vendors have offered connections to these phones. However, feature, function and security limitations may arise when third-party phones are deployed.
Learn More About SIP
For more details on SIP - or for online training and certification - visit The SIP School.

But before you embark on the path of SIP trunking and SIP phones, it's useful to know what SIP is and how it's used, along with some advantages and potential concerns.
What SIP Does and Doesn't Do
Although often thought to be intended specifically for use with voice-over-Internet- Protocol (VoIP) communications, SIP can also be used to establish and control video, instant messaging (IM), file transfer, games and other media sessions. It is used in computer-telephony integration (CTI) applications, connecting IP telephony systems to enterprise server applications such as IBM Sametime and Microsoft Office and Lync products. Some IP PBX vendors use SIP to communicate with VoIP gateways, others for trunking between their IP PBXs.
SIP has five main functions:

- It locates the user and determines which end system will be used in the proposed session.
- It then learns the user's availability (is the user busy; can he/she be disturbed?).
- It determines the capabilities available at the user end system for the session such as what media is supported.
- It establishes the session.
- It manages the session, handling call termination, call transfer, changes to session parameters, and so forth.
SIP does not define a phone call. Rather, a complementary protocol, the Session Description Protocol (SDP) in IETF RFC 4566, defines the many forms of multimedia to be carried over the SIP connection (see box).
Replacing the Local PSTN Connection
As an alternative to traditional PSTN connections, SIP allows the enterprise's IP PBX to communicate directly over an IP connection provided by a SIP trunking service provider, eliminating the need for a enterprise-resident gateway device. The service provider performs the VoIP-to-PSTN conversion.
Key reasons for moving to SIP trunking are lowering costs compared to T1/PRI trunks by 10% to 70%, according to some providers; the ability to offer new services such as combined Internet and voice services; and the ability to offer services in more flexible ways. The enterprise can subscribe to any number of voice connections in small increments from 2 to 700 lines per SIP trunk rather than 24 lines at a time for a T1 connection.
But SIP trunking isn't quite "plug-and-play." Especially during its first year of use, SIP can generate more trouble tickets than T1/PRI trunks because of potential SIP and codec interoperability failure and call-quality issues, which are all highly dependent on the service provider and your premises equipment. Both IP PBX and service provider interface configurations may not match.
Because of the interoperability concerns, it is critical to know whether the prospective SIP trunking provider supports the SIPconnect Technical Recommendation, a standards-based approach for IP peering between SIP-enabled IP PBXs and VoIP service provider networks.
Some vendors have developed their own proprietary SIP trunking support mechanisms that are not compatible with SIPconnect. Before connecting to a service provider, make sure that the provider supports true SIPconnect interoperability rather than a non-standard version of this trunking protocol.
What About Security?
Security is a major concern with SIP trunking. Like any other Internet connection, the SIP trunk should operate through a DMZ. Many SIP users have embraced the Session Border Controller (SBC) as better suited than typical firewalls to providing a security solution. An SBC provides:
- The firewall rule set while also mapping layer 5 to layer 7 addresses
- Intrusion detection and prevention
- Denial-of-service (DoS) attack prevention
- VPN separation for shared resources
- SIP-Transport Layer Security (TLS) handshaking for authentication and encryption of SIP signaling
- Secure Real Time Protocol (RTP) support
- Support for IPsec tunnels
- Transcoding, or conversion between different VoIP codec technologies
Beware of Proprietary End Points
Traditionally IP PBX vendors have developed their own protocols for use with their own brands of IP phones; in addition, Skype and some other voice services have proprietary protocols with SIP-like functionality. As an array of third-party vendors has emerged with new IP phones, most IP PBX vendors have offered connections to these phones. However, feature, function and security limitations may arise when third-party phones are deployed.
Learn More About SIP
For more details on SIP - or for online training and certification - visit The SIP School.










Great article. I'm sharing with a few sale folk.
In my experience, part of the problem with adoption of SIP if the lack of understanding of the infrastructure required to be successful. Sales reps haven't grasped the concept of a SBC and assume the firewall can handle it. This sets us techies up for failure.
The carriers aren't really helping here either. As an example, just yesterday I was in a conference call where the carrier (as in 'Major carrier') actually recommended bypassing the firewall altogether.
Educating our sales force as well VAR and end user tech staff is critical. Once there is a firm grasp of what needs to be in place to make all this happen then I think adoption will happen much easier.
Ralph
www.MitelForums.com