- A TechNote on Wireless and Mobility
- Joanie M. Wexler
- Technology Analyst/Editor
Many businesses are still in the investigation and early-deployment phases of the mobile device management (MDM) craze. Yet suppliers are already forging ahead with yet another approach to taming enterprise mobility risks: mobile application management (MAM).
MAM involves building policy fortresses around certain mobile applications on smart phones, tablets, and laptops to prevent corporate apps from leaking confidential data. Why the sudden focus on MAM? And isn't security, in part, what MDM is already supposed to handle? Let's sort it out.
A Matter of Different Ownership Models
It turns out that employee-owned (a.k.a., "bring your own device," or "BYOD") smart phones and tablets sometimes require different management and security methods than devices procured and deployed by the corporate IT department. Those devices, called corporate-liable devices, are well served by MDM, which is reasonably mature from a product and technology standpoint and encompasses the following functions at the device (rather than the app) level:
MDM requires a client application to be installed on end-users' mobile devices. That's a piece of cake if the company procures, images, and issues the devices itself. IT also can match up existing LDAP or Active Directory user profiles with mobility policies.
However, in BYOD situations, some users are resistant to Big Brother installing software on devices they bought with their own hard-earned cash. That software gives IT the ability to delete users' personal emails, photos, and videos and generally mess with their settings if it's in the best interest of the company. For example, IT might disable a certain feature for security reasons, and that feature might have been the primary reason the user bought that specific device in the first place.
In addition to BYOD users, "Think of the people who work with you but not for you," says John Dasher, vice president of products and marketing at AppCentral, a MAM company in San Francisco. These folks include business partners, resellers, and others who aren't in the company's user database. Your company might wish to make certain applications available to them via an enterprise app store but retain control over the data stored in the app.
Otherwise, risky leakages could occur when one app inappropriately shares data with another "under the covers" on a social networking site. Or when a user cuts and pastes data from an app into an email. On an app-by-app basis, policies need to be applied governing whether these and other actions are allowable.
Unlike MDM, "MAM doesn't touch employees' [or partners'] personal data or personal apps. It only touches enterprise apps," Dasher explains.
Potato versus Potahto
 To be clear, many MDM suppliers include MAM offerings in their portfolios. Among them are Fiberlink/MaaS360, Good Technology, MobileIron, SAP, and Zenprise. In these cases, MAM could be considered a subset of the MDM toolset.
To be clear, many MDM suppliers include MAM offerings in their portfolios. Among them are Fiberlink/MaaS360, Good Technology, MobileIron, SAP, and Zenprise. In these cases, MAM could be considered a subset of the MDM toolset.
There are other companies that focus on the application data aspects of mobility only such as AppCentral, AppGuardian, Enterproid, Fixmo, Mocana, and Nukona (now owned by Symantec). Some, for example, provide a simple mobile development platform for baking the appropriate data-sharing, cut-and-paste, app encryption, and other security policies directly into each app.
There are other alternatives. The exact terminology has still to gel, but the following methods are emerging to help protect enterprise app data while leaving the rest of the user's mobile computer alone:
The distinctions among all these similar-sounding approaches are blurry. One reason, points out James Naftel, senior director, platform solutions management, at MDM/MAM company SAP, is that are no formal mobile security app standards today. Still, you'll want to investigate these options as you endeavor to keep mobility in line with your governance, risk, and compliance (GRC) programs and to prevent costly and potentially reputation-damaging enterprise application data leaks.
This TechNote is brought to you in part due to the generous support of:
MAM involves building policy fortresses around certain mobile applications on smart phones, tablets, and laptops to prevent corporate apps from leaking confidential data. Why the sudden focus on MAM? And isn't security, in part, what MDM is already supposed to handle? Let's sort it out.
A Matter of Different Ownership Models
It turns out that employee-owned (a.k.a., "bring your own device," or "BYOD") smart phones and tablets sometimes require different management and security methods than devices procured and deployed by the corporate IT department. Those devices, called corporate-liable devices, are well served by MDM, which is reasonably mature from a product and technology standpoint and encompasses the following functions at the device (rather than the app) level:
- Provisioning
- Authenticating user access
- Wiping data from missing devices
- Asset tracking
- Setting and enforcing usage policies
- Device encryption
MDM requires a client application to be installed on end-users' mobile devices. That's a piece of cake if the company procures, images, and issues the devices itself. IT also can match up existing LDAP or Active Directory user profiles with mobility policies.
However, in BYOD situations, some users are resistant to Big Brother installing software on devices they bought with their own hard-earned cash. That software gives IT the ability to delete users' personal emails, photos, and videos and generally mess with their settings if it's in the best interest of the company. For example, IT might disable a certain feature for security reasons, and that feature might have been the primary reason the user bought that specific device in the first place.
In addition to BYOD users, "Think of the people who work with you but not for you," says John Dasher, vice president of products and marketing at AppCentral, a MAM company in San Francisco. These folks include business partners, resellers, and others who aren't in the company's user database. Your company might wish to make certain applications available to them via an enterprise app store but retain control over the data stored in the app.
Otherwise, risky leakages could occur when one app inappropriately shares data with another "under the covers" on a social networking site. Or when a user cuts and pastes data from an app into an email. On an app-by-app basis, policies need to be applied governing whether these and other actions are allowable.
Unlike MDM, "MAM doesn't touch employees' [or partners'] personal data or personal apps. It only touches enterprise apps," Dasher explains.
Potato versus Potahto
 To be clear, many MDM suppliers include MAM offerings in their portfolios. Among them are Fiberlink/MaaS360, Good Technology, MobileIron, SAP, and Zenprise. In these cases, MAM could be considered a subset of the MDM toolset.
To be clear, many MDM suppliers include MAM offerings in their portfolios. Among them are Fiberlink/MaaS360, Good Technology, MobileIron, SAP, and Zenprise. In these cases, MAM could be considered a subset of the MDM toolset. There are other companies that focus on the application data aspects of mobility only such as AppCentral, AppGuardian, Enterproid, Fixmo, Mocana, and Nukona (now owned by Symantec). Some, for example, provide a simple mobile development platform for baking the appropriate data-sharing, cut-and-paste, app encryption, and other security policies directly into each app.
There are other alternatives. The exact terminology has still to gel, but the following methods are emerging to help protect enterprise app data while leaving the rest of the user's mobile computer alone:
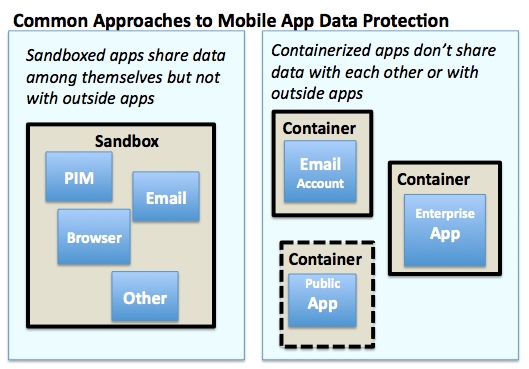
- Sandboxing. Roping off some or all business apps using encryption and policy. Usually the apps within the sandbox can share data among themselves, but not with other apps outside the sandbox.
- Containerization. Partitioning select business applications so they can't inherently share data. The Apple iOS mobile operating system is built on this model. Approaches are also emerging to enable secure data sharing appropriately among the containers. Good Technology, for example, announced AppKinetics in July, a MAM capability that creates an SSL tunnel between each containerized app.
- App wrapping. Applying a management layer and set of policies to a mobile app or set of apps without requiring any changes to the underlying application.
- Dual-persona. Duplicating apps and designating one "corporate" and one "personal" on the user's device. The user switches between the two depending on what mode he is operating in at the moment.
- Virtualization. An emerging model whereby two separately invoiced accounts for users' personal use and corporate use are associated with a single device. Data doesn't penetrate account "walls."
The distinctions among all these similar-sounding approaches are blurry. One reason, points out James Naftel, senior director, platform solutions management, at MDM/MAM company SAP, is that are no formal mobile security app standards today. Still, you'll want to investigate these options as you endeavor to keep mobility in line with your governance, risk, and compliance (GRC) programs and to prevent costly and potentially reputation-damaging enterprise application data leaks.
This TechNote is brought to you in part due to the generous support of: